Magic NFC business card
Clone access control cards in few seconds having just Android phone and my special business card - catch me at various events to get one!
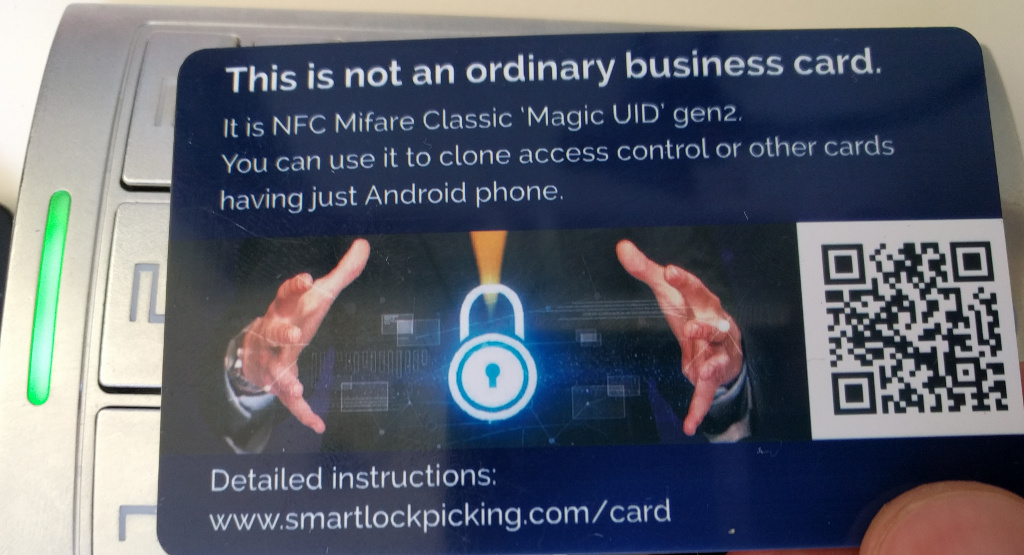
Many access control systems still rely just on the UID of the card. It is a unique number, generated during manufacturing, read-only and impossible to change. There are however special, unofficial “Magic UID” cards (like my business card) that allow to set any UID - clone it from other cards. It takes just a few seconds with the new “one click” cloning feature that I have contributed to free Mifare Classic Tool Android application.
How to clone UID using this card?
You will need Android phone, and it will work for Mifare Classic cards. A short video of this process:
Android phone
You need to have Android phone with supported NFC chipset. Most current Android phones should be OK. A non-exhaustive list of devices confirmed to work is here.
Mobile application
Install free, opensource Mifare Classic Tool from Google Play: https://play.google.com/store/apps/details?id=de.syss.MifareClassicTool:
The one-click cloning feature is available starting from version 2.3.0, released 4.05.2019.
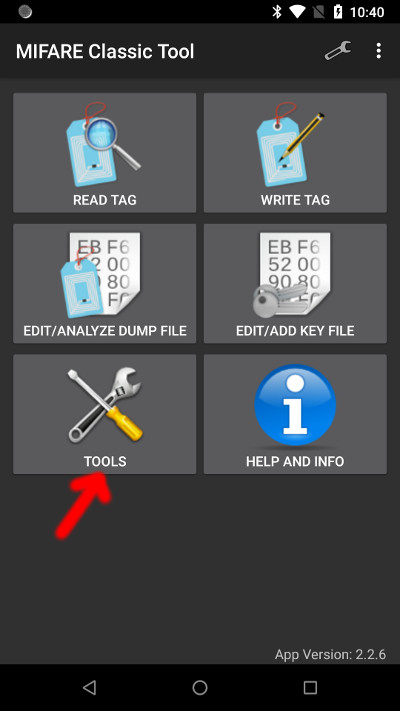
Step-by-step instruction
In the Mifare Classic Tool choose Tools -> Clone UID:
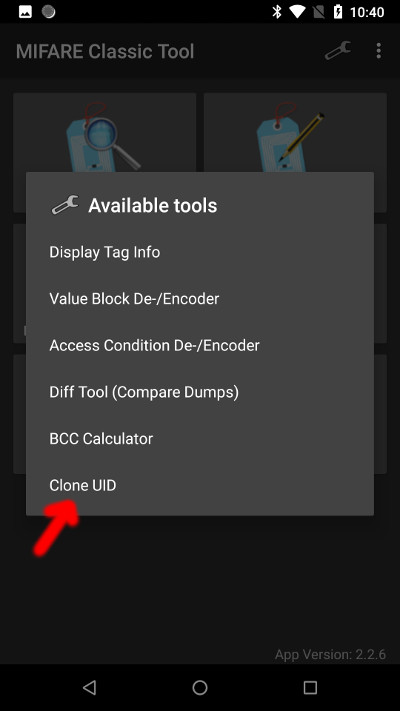
The cloning function:
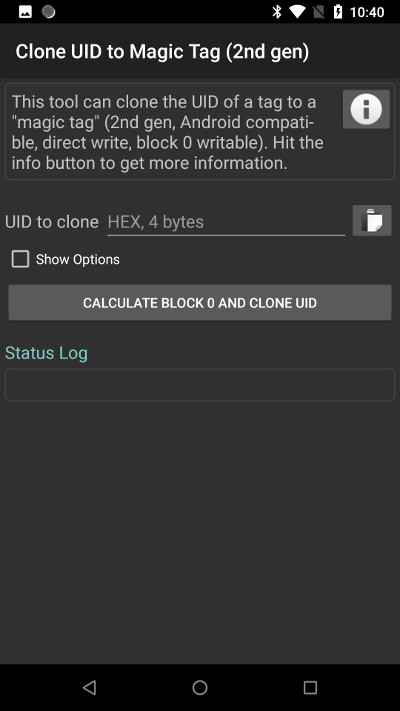
Swipe the original card at the back of your phone, the application should recognize it and fill the UID value automatically. Press “Calculate block 0 and clone UID” button:
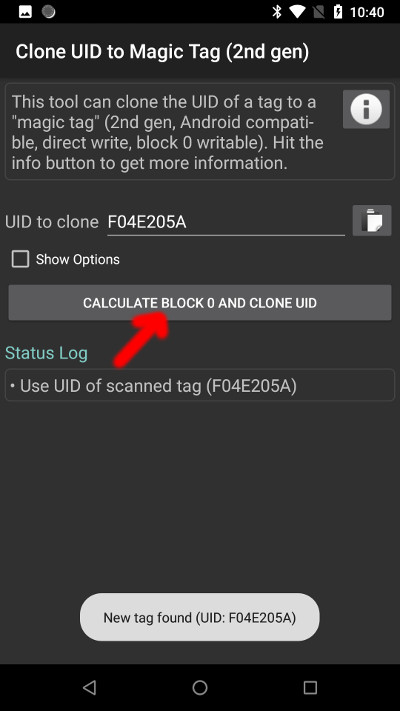
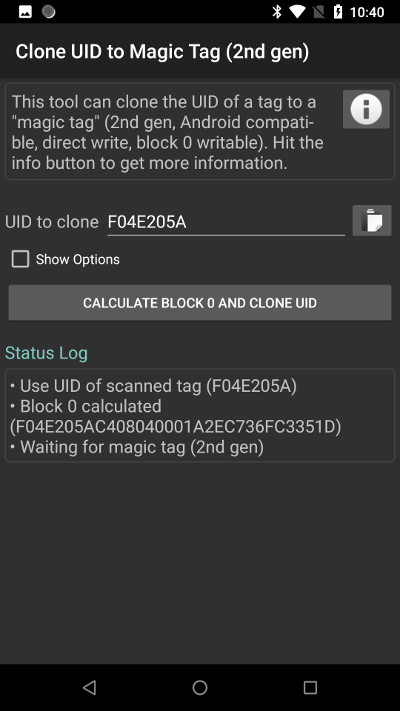
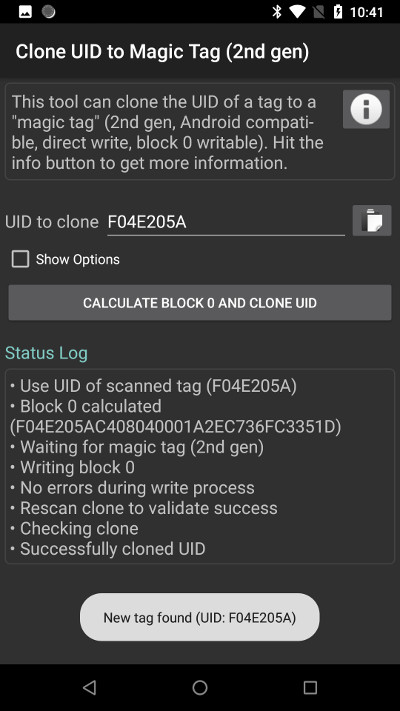
Now swipe the “magic” card at the phone. It will write the new UID to card, and then verify if the operation was successful (in some cases you may need to swipe the cloned card again at the phone):
Where does it work?
It has been confirmed to work not only in office buildings, parking gates and apartments, but also in some hotels:
@slawekja gave me his business card. Now I have spare key for my hotel at @CONFidenceConf. 😉 So much for "403 - Forbidden" 😁 #CONFidenceConf pic.twitter.com/FXJHNAPRT0
— Gerhard Klostermeier (@iiiikarus) June 3, 2019
It work great. Thanks to @slawekja 🙄👍 pic.twitter.com/3dh7NHNi1P
— Kevin2600 (@Kevin2600) October 11, 2019
@slawekja device has been tested in Russia. It's official, it works! https://t.co/9ZvV2pLP6F pic.twitter.com/zEOIrgpGsQ
— Timur Yunusov (@a66ot) December 10, 2019
Let me know if it worked for you as well!
FAQ
Where can I get this card?
Catch me up at any of the upcoming events, and I will give it to you as my business card.
You can also buy such card yourself, they are available from various sellers. Please note there are two generations of “Magic UID” cards. The first generation requires special, “backdoor” commands to unlock this cloning functionality. These commands are not compatible with Android phone. You need to have “Magic UID gen2” or “direct write to block 0” cards, compatible with Android, with no “backdoor” commands.
Is it possible to clone also data of the card?
Yes, depending on the card keys configured it may be possible to read the data also using Mifare Classic Tool (“Read Tag” function). For other cases, more advanced hardware (starting at $5) will be required. Next, you can write the exact copy of the original card (including “manufacturer block 0”) to “magic card”, using “Write Tag” function.
Will it work for other types of cards?
No, this will only work for Mifare Classic, 4-byte UID (most commonly used). There are however many other ways to clone cards using some other equipment, and it is quite likely that your other type of card can be easily copied, too.
Want to learn more?
Have a look at my presentation - introduction to NFC security: “A 2018 practical guide to hacking RFID/NFC” slides (PDF), youtube recording.
Interested in a training regarding security of RFID/NFC, Bluetooth Low Energy (Smart), Android NFC Host Card Emulation, KNX home automation, Linux embedded, and many other topics? Check out previous and upcoming events or contact us for a private training. It may make sense for a group even as small as 3 people.
Share this post
Twitter
Google+
Facebook
Reddit
LinkedIn
StumbleUpon
Email