HackInParis training
Smart lockpicking - hands-on exploiting IoT devices based on access control systems

Learn how to assess and secure IoT devices by having fun with hacking a dozen of devices among most profitable to attack - smart locks. The agenda will include: wireless sniffing, spoofing, cloning, replay, DoS, authentication and command-injection attacks, analyzing proprietary network protocols, breaking “Latest PKI technology”, abusing excessive services… The software-focused activities will be mixed with short entertaining tricks like opening lock by a strong magnet, counterfeiting fingerprints in biometric sensor or opening voice-controlled lock by hacking nearby speaking toys. Technologies covered will include: Bluetooth Smart, Linux embedded, KNX, NFC, WiFi, P2P, GSM, Wiegand, and others. Each student will receive a 100 EUR value hardware, consisting of Bluetooth hardware sniffer, Raspberry Pi configured with tools and Hackmelock for further practice at home.
Pre-requisites
- At least basic familiarity with Linux command-line, Kali, Wireshark.
- Scripting/programming skills will be very helpful.
- Mobile application reversing skills will be an advantage.
Target audience
- Pentesters, security professionals
- IoT developers
- Anyone interested
Material to bring by attendees
Contemporary laptop with virtualization software able to run Kali Linux (at least 4GB of RAM, 40GB space), Android > 4.3 smartphone
Course syllabus
Bluetooth Smart
based on 7 various smart locks, and specially developed Hackmelock (consisting of Android mobile application and lock device simulated on Raspberry Pi):
- passive sniffing - hardware, software
- active MITM - learn GATTacker BLE proxy tool from its creator; BTLEjuice
- static authentication password capture
- spoofing devices and their status
- replay attacks
- command injection
- Denial of Service
- cracking “latest PKI technology”
- other flaws of custom challenge-response authentication
- abusing excessive services (e.g. module’s default AT-command interface).
- weaknesses of access sharing functionality
Linux embedded
based on wireless doorlock, alarm+home automation system
- authentication bypass
- information disclosure
- telnet brute-force
- command injection
- physical attack: switching to WiFi maintenance mode using external intercom
- UART interfaces
Proprietary network protocols
based on several devices (fingerprint sensor, time attendance monitor, wireless doorlock, alarm system)
- methods of analyzing proprietary protocols - sniffing, MITM, reversing client/server
- sniffing administrative credentials
- abusing improper session management - authentication bypass
- P2P feature - how to attack doorlock hidden behind NAT
- taking control over proprietary HVAC control appliance
Home automation systems
integrated with alarms, doors and access control - based on KNX example installation provided
- typical architecture, group address, device address, KNX-IP gateway
- tools: ETS configuration software, knxmap, nmap scripts…
- locate KNX gateway in LAN or remotely from the Internet
- monitor mode - sniffing the bus passively
- sending write command to group address and open connected doorlock
SMS and voice remote control over GSM
based on remote control alarm system
-
brute-force alarm PIN via SMS and voice calls
NFC/RFID
based on hotel electronic door lock, pinpad, time attendance sensor
- clone contactless card
-
brute-force ID
Wiegand
- sniff the data transmitted from access control reader using BLEKey
Moreover
everyone will also be able try oneself to:
- open smart lock using strong magnet influencing the motor
- cheat fingerprint biometric sensor - you can make your own fingerprint clone
- open voice-controlled lock by hacking nearby speaking devices
Several exercises will be connected with electronic lock guarding a special box of goods from Poland. Whenever a participant will succeed in hacking the lock, the box opens automatically, and one can have a delicious cookie or a shot of a Polish vodka :)
What will be provided?
-
course materials in PDFs (several hundred pages) -
all required additional files: source code, documentation, installation binaries... -
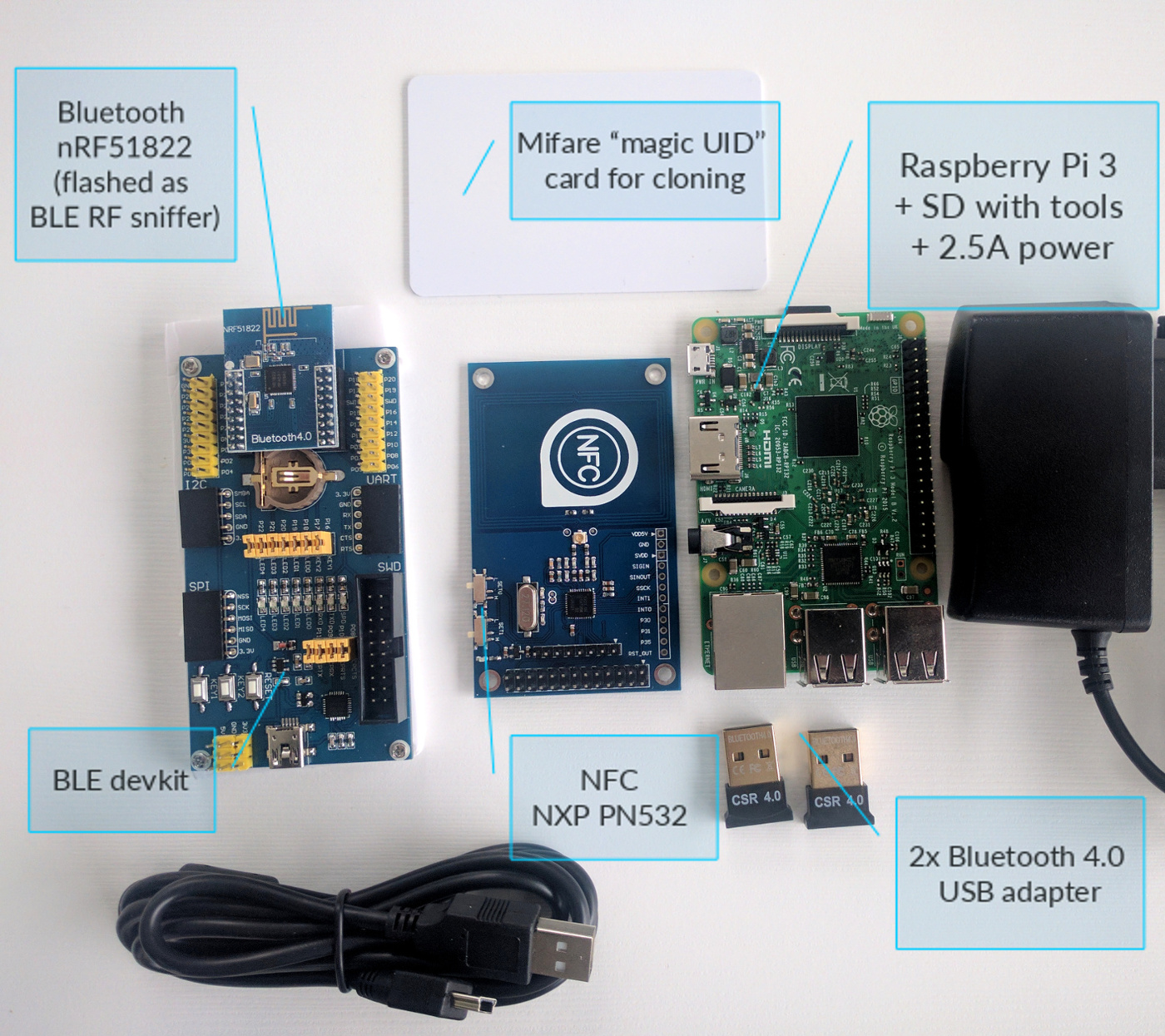
Bluetooth Smart hardware sniffer and development kit based on nrf51822 module -
2 Bluetooth Low Energy USB dongles -
Raspberry Pi 3 with assessment tools and Hackmelock for further hacking at home -
NFC NXP PN532 board + "magic UID" card - which will allow you to clone most common Mifare Classic contactless cards
Register here:
https://hackinparis.com/store/order/?product=52&option=bundle
Share this post
Twitter
Google+
Facebook
Reddit
LinkedIn
StumbleUpon
Email