HackInParis 2019 workshops
Cracking Mifare Classic on the cheap; A 45min introduction to Bluetooth Low Energy

During upcoming HackInParis 2019 I will present a series of introductory workshops about security of NFC Mifare Classic and Bluetooth Low Energy. The workshops are short (45min each session), but packed with practical knowledge and hopefully entertaining - performed on a real access control installation, hotel lock and BLE smart locks. Most hands-on exercises will be possible to complete using just a phone, and easy to follow.
Slides
Cracking Mifare Classic on the cheap - workshop (PDF, 4M)
A 45min introduction to Bluetooth Low Energy - workshop (PDF, 6M)
Details
Cracking Mifare Classic on the cheap
Despite several vulnerabilities and upgrade advisories published years ago, Mifare Classic is still surprisingly often used for access control, bus tickets, loyalty cards or e-wallets. During this workshop, you will learn how to crack and clone it using just a mobile phone or an inexpensive hardware.
We will cover:
- Mifare Classic introduction: UID, keys, security, data sectors, blocks
- clone card UID in 2s to “magic NFC” gen2 business card using just a phone (on real access control installation)
- brute-force of the common, dictionary keys using Mifare Classic Tool and mobile phone, clone hotel card and test at real hotel door lock
- cracking Mifare Classic and Mifare Classic EV1 using nested, darkside and hardnested attacks (libnfc PN532)
Hardware set
We will perform the exercises using following hardware set:

For your convenience, several hardware sets will be available to get during the workshop for only 10 EUR (the same price they have been imported from China).
A 45min introduction to Bluetooth Low Energy
You will learn how to discover and interact with nearby BLE devices using just mobile phone - what in so many cases equals “hacking” them, as there is no security at all.
We will cover:
- short introduction to Bluetooth Low Energy
- advertisements, beacons
- services, characteristics
- reading, writing, notifications
- “hacking” BLE dildo and smart locks
- BLE400 development board, sample code of device to attack, flashing different firmware (sniffer, jammer/hijacker)
Following the workshop, you will be able to try more advanced topics (e.g. sniffing and attacking your device), using provided “homework” materials.
Hardware set
We will perform the exercises using following hardware set:
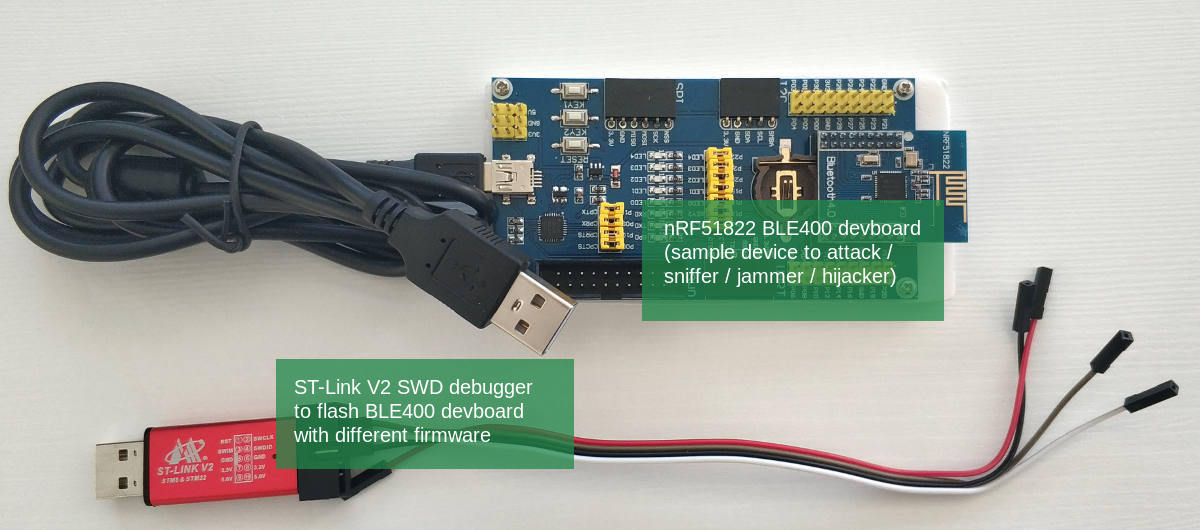
For your convenience, several hardware sets will be available to get for only 15 EUR (the same price they have been imported from China).
Hardware errata
After the workshop, I became aware that some of the ST-Link programmer devices I have included in the BLE hardware sets, have incorrect labels. I am very sorry for this inconvenience - apparently the low price from China comes at a cost of quality.
Fortunately, the devices are working correctly, only the labels are incorrect. In case your programmer’s labels are like the green one on the right:

please just connect the wires according to the red markings: SWCLK where label is SWDIO, SWDIO where label is GND, and GND where label is SWCLK. If you still have trouble with the setup, please contact me.
When and where?
The workshops will take place during HackInParis (Maison de la Chimie), in room 69 on the main floor (floor plan). There will be several editions, and the times are scheduled to match the conference talks happening at the same time. You are welcome to join any time that suits you.
Day 1 - Wednesday, 19th June
| 9:30 - 10:15 | Cracking Mifare Classic on the cheap |
| 10:15 - 11:00 | A 45min introduction to Bluetooth Low Energy |
| 11:00 - 11:25 | Coffee break |
| 11:25 - 12:10 | Cracking Mifare Classic on the cheap |
| 12:10 - 12:55 | A 45min introduction to Bluetooth Low Energy |
Day 2 - Thursday, 20th June
| 13:45 - 14:30 | Cracking Mifare Classic on the cheap |
| 14:30 - 15:15 | A 45min introduction to Bluetooth Low Energy |
| 15:15 - 15:40 | Coffee break |
| 15:40 - 16:25 | Cracking Mifare Classic on the cheap |
| 16:25 - 17:10 | A 45min introduction to Bluetooth Low Energy |
I’m in, what should I bring?
The workshops are designed to be quick to set up and easy to follow. About 90% of practical exercises will be possible to perform using just a phone (preferably Android) and free mobile applications. We will use:
- Mifare Classic Tool (Android only)
- nRF Connect
But even if you don’t have Android phone - don’t worry, a few preconfigured ones will be available.
Some more advanced tasks are designed to solve with laptop and Linux (virtual machine), but bringing it is not actually necessary. You will be able to finish these exercises at home with provided hardware set.
You are welcome to bring also your own Mifare Classic cards or BLE devices to check their security.
Share this post
Twitter
Google+
Facebook
Reddit
LinkedIn
StumbleUpon
Email