Bluetooth Smart Hackmelock
Open-source vulnerable device and mobile application for training

Bluetooth Smart locks did not have a good press recently regarding their security. One of the reasons may be lack of knowledge, as well as insufficient number of professionals to assess and secure such devices. This project helps to develop relevant skills and allows to practice BLE hacking without the need of having the physical vulnerable hardware.
Components and requirements
Hackmelock consists of two main components: vulnerable Bluetooth Smart lock device - emulated in software, and Android mobile application which connects to the device. The Bluetooth communication between the mobile application and the emulated “peripheral” lock device works exactly the same as with a real smart lock.
Emulated device
This part is written using Node.js Bleno package . The code is tested to run on Linux (including Debian, Kali), and on Raspberry Pi. It should work on OS X, and maybe also Windows - but these configurations have not been tested.
You will just need a Bluetooth 4 adapter. If you have contemporary laptop, chances are such adapter is already built-in. You can check if it supports Bluetooth version 4.0 by issuing following commands from Linux:
$ hciconfig
hci0: Type: BR/EDR Bus: USB
BD Address: D0:39:72:B7:AD:88 ACL MTU: 310:10 SCO MTU: 64:8
UP RUNNING
RX bytes:6748 acl:209 sco:0 events:332 errors:0
TX bytes:4756 acl:209 sco:0 commands:109 errors:0
$ hciconfig hci0 version
hci0: Type: BR/EDR Bus: USB
BD Address: D0:39:72:B7:AD:88 ACL MTU: 310:10 SCO MTU: 64:8
HCI Version: 4.0 (0x6) Revision: 0x22bb
LMP Version: 4.0 (0x6) Subversion: 0x22bb
Manufacturer: Cambridge Silicon Radio (10)
In the above example the adapter supports 4.0 - HCI Version: 4.0 (0x6).
You can also use Raspberry Pi 3, which has embedded adapter confirmed to work. Or, use an external USB dongle, e.g. CSR-8510-based (cost around 5$).
Android mobile application
Android application works as a “master” Bluetooth device, and connects to the emulated lock using Bluetooth Low Energy - just like it would connect to a real lock.
Installation
Emulated device in Linux
Install prerequisites: node.js, npm, and bleno libraries. More information: https://github.com/sandeepmistry/bleno#prerequisites
Debian/Ubuntu/Kali
$ sudo apt-get install nodejs nodejs-legacy npm bluetooth bluez libbluetooth-dev libudev-dev
Raspberry Pi
Current Raspbian offers Node.js version 0.10, but bleno requires version at least 4.x. Follow these steps:
$ sudo apt-get remove --purge node* npm*
$ curl -sL https://deb.nodesource.com/setup_4.x | sudo bash -
$ sudo apt-get install nodejs libbluetooth-dev bluez-hcidump bluez-tools
Get the device code
Install the hackmelock device:
$ npm install hackmelock
alternatively, you can clone it from Github, and then install required Node.js modules:
$ git clone https://github.com/smartlockpicking/hackmelock-device
$ npm install bleno colors async
Mobile application
Install the Android mobile application from Google Play Store:
https://play.google.com/store/apps/details?id=com.smartlockpicking.hackmelock
Or download APK binary here.
You can also build it yourself from sources available on Github.
Mobile application privacy policy
The mobile application requires permissions:
Location access
Starting from Android 6.0 this permission is required to scan for Bluetooth devices. Your location is NEVER collected, stored nor sent to any external service in any way. It is just necessary to scan for local BLE devices.
Camera
In order to scan QR code for guest sharing access functionality, the mobile application requires permission to use a camera. Again, picture from camera is not stored nor shared with any external service - it is just used locally by QR code processing barcode scanner.
I encourage you to check Android source code available on Github, or compile the application yourself.
Usage
In order to run emulated device, first stop bluetoothd service in your system, as it may interfere with bleno library (See also: https://github.com/sandeepmistry/bleno#prerequisites), next power up the Bluetooth interface by hand:
$ sudo systemctl stop bluetooth
$ sudo hciconfig hci0 up
Running the device emulator:
$ cd node_modules/hackmelock
$ node peripheral
advertising...
If you don’t see advertising... line, your Bluetooth adapter may be offline.
You can also check if the device is advertising properly using nRF Connect application:
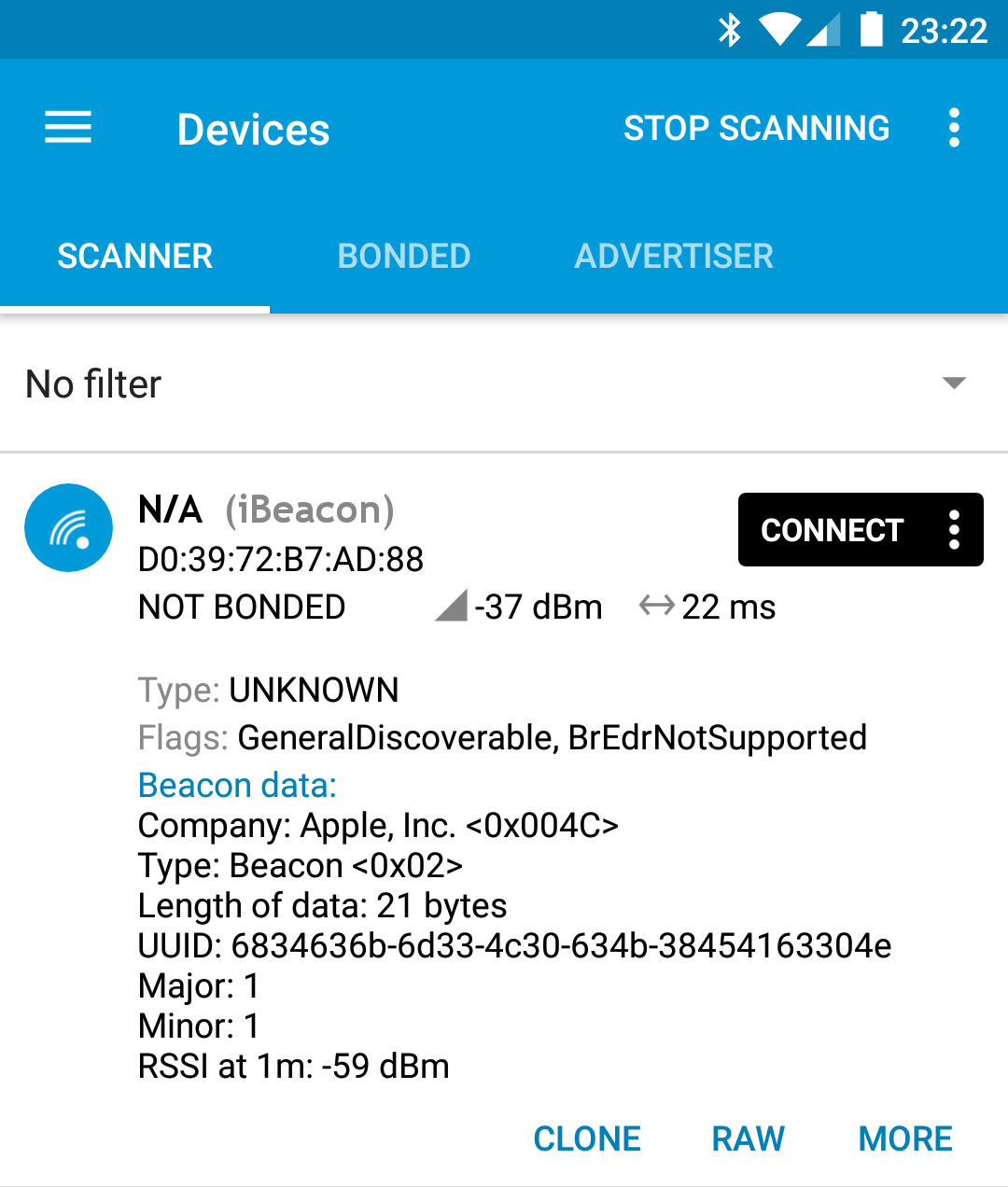
In initial configuration mode it advertises as iBeacon with UUID 6834636b-6d33-4c30-634b-38454163304e and Major/Minor set to 1.
Pairing (first use)
Start Android application. Choose “Setup new lock”:
The application requires location access - as starting from Android 6.0 this permission is required to scan for Bluetooth devices. Don’t worry - it is not a trick and your location is not collected in any way - check Android source code available on Github yourself!
The application starts scanning for hackmelock emulated devices which advertise configuration mode (iBeacon Major/Minor=1). As soon as it discovers such device, it is displayed along with its MAC address:

After connecting the application starts pairing procedure:

On the device console you should see the initialization configuration progress:
$ node peripheral.js
advertising...
Client 4a:00:e9:88:16:63 connected!
Status read request:
Initialization mode!
initializing... 0 531ce397
initializing... 1 325d18fe1481151073dc4d4a
initializing... 2 7ca71db0196bda712131dc57
initializing... 3 57a604c2f29fbe939a628ee1
initializing... 4 04124d2718c5025b2e313f38
initializing... 5 677d07466c933b50a4ff25d8
initializing... 6 cc326b6cd47ef976bb36c039
initializing... 7 a7954e5dbfa47471e46b6a58
initializing... 8 d2b6d0895e1a7c10485cc09e
initializing... 9 7cba1aaacd5f2300da2068af
initializing... 10 c5a1dd31b5844e44c3972c97
initializing... 11 0b2bd0f0ccf79128c5a7cf07
initializing... 12 6e1ab5b4b287194d3927dee3
initializing... 13 898f201f15b83b579e8bd1b1
initializing... 14 d536a58292db1008aea1fb15
initializing... 15 025b69cb4436d9d5eb27838e
initializing... 16 ff11b8fa89e27cfc74cf2294
initializing... 17 aa1fbc2229975bf8cf9707f7
initializing... 18 bc3c5c2815932c7f0fe891da
initializing... 19 128c1fa3ac2584b83237787a
initializing... 20 9969a4f1bd5f037b3af5e069
initializing... 21 f82315b43210d32fec64141a
initializing... 22 c9cac5b02f9cbac394d0ec97
initializing... 23 1a4da9c71be6d0a8452c0bdf
initializing... 24 31bd687706b69e9255c0835e
Config loaded - iBeaconMajor: 21276 iBeaconMinor: 58263
From now on, the lock device is paired, configuration is stored in config.txt file.
Next time running the emulator node peripheral will advertise specific IDs, loaded from configuration file:
$ node peripheral
Config loaded - iBeaconMajor: 21276 iBeaconMinor: 58263
advertising...
Lock control
After connecting, you can open and close the lock. Administrator can also synchronize data:

Sharing
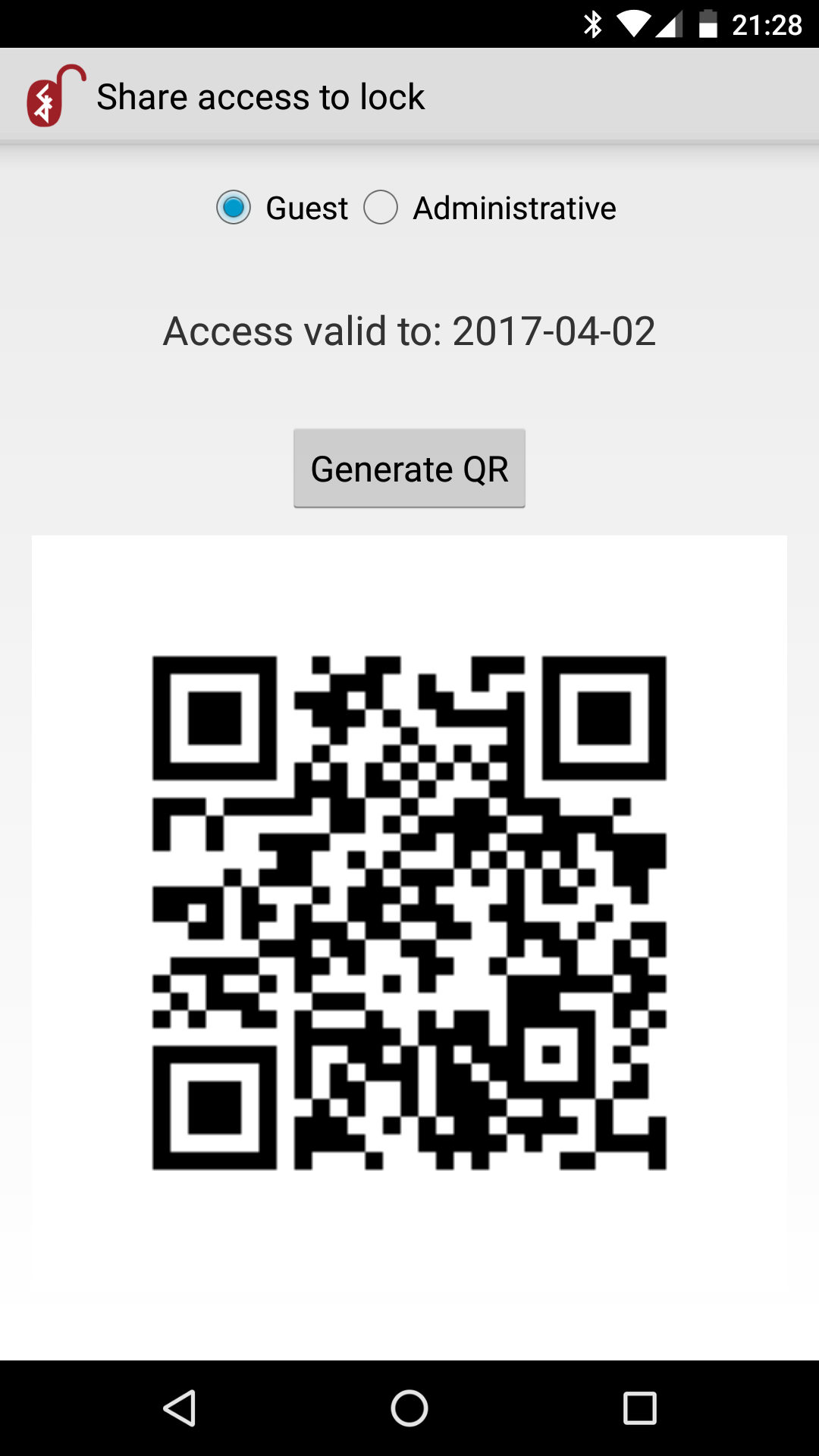
Administrator can share access to the lock with others. It is possible to share guest or administrative access. The access is granted for limited time:
The generated QR code has to be passed to the guest, and next scanned by choosing option: “I have QR code” available after installing application:
Application running on the guest’s device will need permission to use the camera - in order to scan the QR.
Resetting configuration
Emulated device
Remove config.txt file, restart.
Android application
At this moment there is no reset configuration functionality implemented. You will need to manually clear application data (Settings -> Apps -> Hackmelock -> Storage -> Clear data), or reinstall the application.
Hacking
The device contains various vulnerabilities, similar to the ones disclosed in real smart locks. Stay tuned for more information and articles on how to hack it.
Troubleshooting/FAQ
Questions, feature requests, issues? Github projects for: hackmelock device and Android application.
Share this post
Twitter
Google+
Facebook
Reddit
LinkedIn
StumbleUpon
Email