Confidence 2018: NFC research toolkit
NFC hackme challenges, and 'A 2018 practical guide to hacking RFID/NFC' talk

During upcoming Confidence conference in Krakow, we will celebrate 15 years of SecuRing. On this occasion the we will share with you several NFC “research toolkits” hardware sets - that among other things allow to clone card UID and crack Mifare Classic. Come meet us at our booth and solve the NFC challenges to win one!
Also be sure to attend my introductory talk on NFC security “A 2018 practical guide to hacking RFID/NFC” track 1 Jun 4th 11:50am.
Update: slides are available to download here.
The kit contents
The kit contains NFC board, USB UART adapter, wires, magic UID card, and two tags to crack.

Assembly
Connect the NFC board to USB UART adapter using provided wires (RX to TX and TX to RX):
| NFC module | USB adapter |
|---|---|
| GND | GND |
| VCC | +5V or 3V3 (will work for any) |
| TXD (SDA) | RXD |
| RXD (SCL) | TXD |
Properly assembled set should look like this:
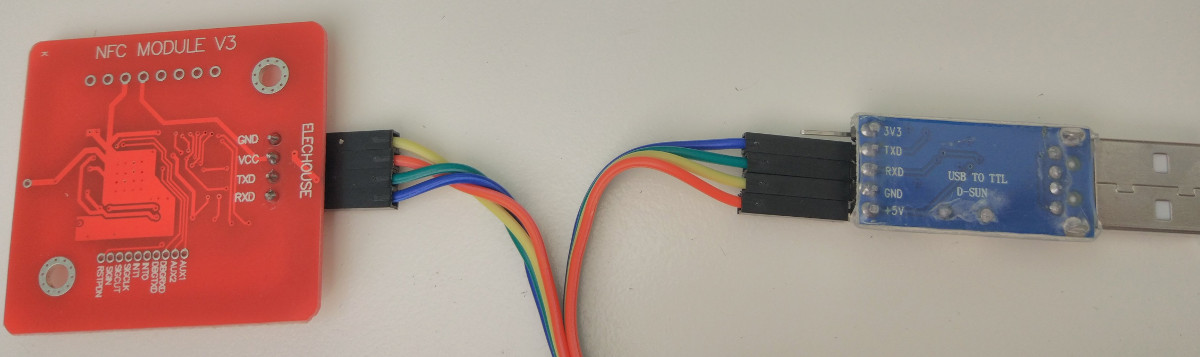
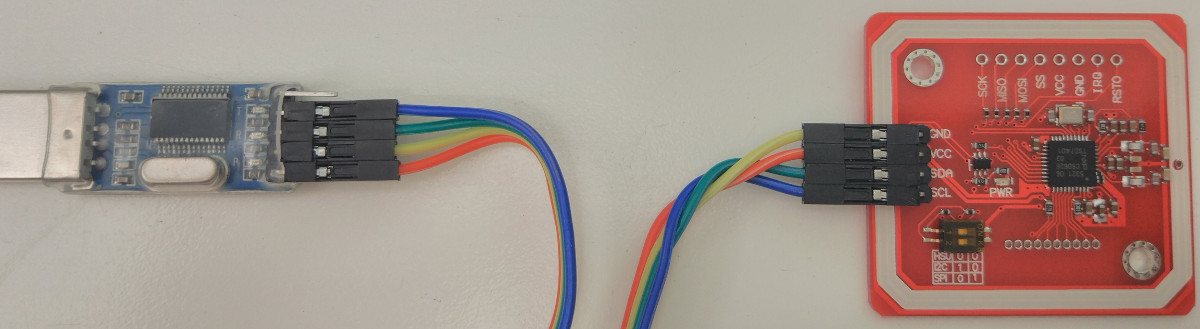
Installation
The following procedure has been confirmed on Kali Linux (you can run it in virtual machine), but should also work on Debian or Ubuntu systems.
Install the required software (it may be already preinstalled in your Kali Linux):
$ sudo apt-get install libnfc-bin libnfc-examples mfoc mfcuk
Connect the USB adapter (in case of using virtual machine, connect “Prolific USB serial adapter” device to it). Check that the device is correctly recognized by system:
root@kali:~# dmesg
You should see something like this:
[298932.656178] usb 1-1.2: new full-speed USB device number 6 using xhci_hcd
[298933.006140] usb 1-1.2: New USB device found, idVendor=067b, idProduct=2303
[298933.006147] usb 1-1.2: New USB device strings: Mfr=1, Product=2, SerialNumber=0
[298933.006151] usb 1-1.2: Product: USB-Serial Controller
[298933.006153] usb 1-1.2: Manufacturer: Prolific Technology Inc.
[298933.141377] usbcore: registered new interface driver usbserial
[298933.142158] usbcore: registered new interface driver usbserial_generic
[298933.142303] usbserial: USB Serial support registered for generic
[298933.147399] usbcore: registered new interface driver pl2303
[298933.147416] usbserial: USB Serial support registered for pl2303
[298933.147437] pl2303 1-1.2:1.0: pl2303 converter detected
[298933.149469] usb 1-1.2: pl2303 converter now attached to ttyUSB0
Notice the ttyUSB device (in the above example: ttyUSB0). Now edit NFC settings to enable the device:
root@kali:~# gedit /etc/nfc/libnfc.conf
Add (or uncomment) the following line to the end of /etc/nfc/libnfc.conf file, substituting ttyUSB matching your one:
device.connstring = "pn532_uart:/dev/ttyUSB0"
Now you can check if the configuration works properly, by issuing command:
root@kali:~# nfc-list
nfc-list uses libnfc 1.7.1
NFC device: pn532_uart:/dev/ttyUSB0 opened
The pn532_uart:/dev/ttyUSB0 opened status means the device works properly, and you can proceed further with our challenges.
In case you encounter following communication error:
root@kali:~# nfc-list
nfc-list uses libnfc 1.7.1
error libnfc.driver.pn532_uart pn53x_check_communication error
nfc-list: ERROR: Unable to open NFC device: pn532_uart:/dev/ttyUSB0
please check the wiring between USB adapter and NFC board.
If the error message is about invalid serial port:
root@kali:~# nfc-list
nfc-list uses libnfc 1.7.1
error libnfc.driver.pn532_uart Invalid serial port: /dev/ttyUSB0
nfc-list: ERROR: Unable to open NFC device: pn532_uart:/dev/ttyUSB0
please check that the USB adapter ttyUSB is properly visible in Linux (see above).
Challenges
We have prepared several challenges.
1. Clone card’s UID
Card UID is most commonly 4-byte value stored on the card. Manufacturer guarantees it is unique and read-only, impossible to change. Multiple access control systems rely solely on this UID - valid card is recognized by reader and the access is granted.
Our NFC toolkit contains special, “magic” card that allows to set the UID to a different one. You can use this card to clone UID of original, valid card.
Come to our booth at conference, get the valid card, place it on the NFC board and check its UID:
root@kali:~# nfc-list
nfc-list uses libnfc 1.7.1
NFC device: pn532_uart:/dev/ttyUSB0 opened
1 ISO14443A passive target(s) found:
ISO/IEC 14443A (106 kbps) target:
ATQA (SENS_RES): 00 04
UID (NFCID1): d4 84 7f 1e
SAK (SEL_RES): 08
in this example, the card UID is d4847f1e.
Next, place the magic card on the NFC board:

And clone the UID using nfc-mfsetuid <target UID> command:
root@kali:~# nfc-mfsetuid d4847f1e
(...)
Found tag with
UID: 01234567
(...)
Sent bits: d4 84 7f 1e 31 08 04 00 46 59 25 58 49 10 23 02 a3 a2
Received bits: 0a
You can check your magic card UID using nfc-list, and if it changed properly try it on our live installation.
2. Clone the card based on its picture
On some cards there are small numbers printed. Guess what the numbers are? Yes, the UID. Usually it is a decimal form of the hex UID, in many cases shortened (e.g. only 3 bytes), sometimes reversed.
Come to our booth at conference, you will receive a picture of a valid card that unlocks the special box.

Your task is to decode the number back to hex UID, and clone it using the magic UID card.
You can use some online converters, or simply translate decimal to hex.
3. Brute force Mifare Classic
Find a value stored in ‘value block’ of a protected sector.
Mifare Classic is one of the most commonly used tags, despite being vulnerable to several attacks. Card data is organized in sectors. For each sector it is possible to configure individual acces key and permissions. Valid access key is stored in a reader, which can read the card data.
For our first Mifare Classic challenge take the blue tag:

There are several sectors protected using factory default key (FFFFFFFFFFFF). Another sector’s keys are in a publicly available dictionary of leaked/default keys.
Using Android mobile application
Dictionary brute-force is possible for example using free Mifare Classic Tool Android mobile application. Your Android phone needs to have NXP NFC chipset (most recent models with a few exceptions), otherwise the app just won’t work. Choose “Read Tag” fuction, then select “extended-std” and “std” key files and hit “Start mapping and read tag”. In a few moments you should have content of most sectors.
Note: if you experience unstability (e.g. “Error: lost connection to the tag”, “Error: there is no tag”, multiple “No key found (or dead sector)” for different sectors every time) - try to place the tag exactly at the NFC phone antenna, or try with another phone.
The “No keys found (or dead sector)” at sector 2 means the key for this specific sector was not found in your brute force dictionary. You can find more up-to-date list of leaked keys here. In order to import it using “Edit/Add Key File” function, you just need to strip it to proper format (just 12 hex chars per each key). You can do it for example using this Linux command:
$ cat default_keys.dic |cut -c1-12 > default_keys.keys
Using our NFC board
You can also use MFOC tool that among other things can brute force the keys. It has a few standard keys embedded, but for our task more comprehensive list of keys will be needed. Download it and execute mfoc with the key file to create resulting card image to dump.img:
root@kali:~# wget https://github.com/iceman1001/proxmark3/raw/master/client/default_keys.dic
root@kali:~# mfoc -f default_keys.dic -O dump.img
If everything goes well, in a few moments you should see:
(...)
We have all sectors encrypted with the default keys..
Auth with all sectors succeeded, dumping keys to a file!
(...)
and have the card data in dump.img.
The resulting dump file is just a binary mapping all the tag’s content, you can view it using any hex editor (e.g. hexedit).
The tag data
Block 0 of sector 0 is the read-only “manufacturer data” - contains among others the card UID. Sector 1 is protected with a simple, dictionary key that is also embedded in Mifare Classic Tool mobile application. Sector 2 key is also leaked, but only in the more dictionary.
In sector 2 you will find a special “value block”. It stores a number value in multiple ways (straight and reversed). You can decode it for example using the Mifare Classic Tool app - it has “value block” decoder/encoder embedded. Remember - if you see “no keys found or dead sector”, you need to update your key file dictionary accordingly.
4. Crack Mifare Classic
For this challenge we have prepared another tag, with some sectors secured using non-dictionary keys.

In order to crack these keys, we will use an attack on Mifare Classic known as “nested”. It is implemented in the MFOC tool that you are already familiar with, and requires at least one known key to any sector.
Place the tag on NFC board and start MFOC - dump resulting card image to dump1.img
root@kali:~# mfoc -O dump1.img
Found Mifare Classic 1k tag
(...)
The tool will try default keys (you can feed additional ones using -f <keyfile> parameter if needed), and then will proceed with cracking. If everything goes well, after several minutes it will find the key:
Using sector 00 as an exploit sector
Sector: 2, type A, probe 0, distance 1578 .....
Sector: 2, type A, probe 1, distance 1583 .....
Found Key: A [REDACTED]
(...)
Auth with all sectors succeeded, dumping keys to a file!
(...)
Once you succeed in cracking all the keys and dumping data, find a secret flag hidden in one of the sectors, and come back to us to claim the reward!
By the way, you can also clone the resulting dump to your magic card:
root@kali:~# nfc-mfclassic W a dump.img
NFC reader: pn532_uart:/dev/ttyUSB0 opened
Found MIFARE Classic card:
(...)
Writing 64 blocks |................................................................|
Done, 64 of 64 blocks written.
Now your magic card is exact copy of the cracked one (including UID).
You can later format your magic card back to blank using nfc-mfsetuid -f command.
Other Mifare attacks
Crack Mifare Classic using “Darkside”
In case you encounter a tag with no default/dictionary keys, using mfoc you will end up with following error:
mfoc: ERROR:
No sector encrypted with the default key has been found, exiting..
You can still crack it using another attack - “darkside”. The relevant tool is MFCUK. The following parameters crack key A to sector 0, and are fine-tuned for our hardware (delays). Expect it to take at least several minutes.
# mfcuk -C -R 0:A -s 250 -S 250 -v 3
The verbosity level (-v 3) will inform you on progress. The diff Nt value should stay as low as possible (preferably below 300), and the auths value should increment.
In case the auths increases equally with diff Nt - most likely you have a tag that is “hardened” against such attacks (e.g. Mifare Classic EV1, or Mifare Plus in MF Classic mode).
Once you crack at least one valid key using mfcuk, you can now proceed with much faster “nested” attack, providing the known key as additional parameter:
# mfoc -k <your_revealed_key> -O dump.img
Mifare Classic EV1 (hardened)
You can also encounter “hardened” Mifare Classic EV1 tags that are not vulnerable to abovementioned (“nested”, “darkside”) attacks. If you have at least one known key to any sector, you can try “hardnested” attack against such tags.
Probably the easiest way to perform this attack is using miLazyCracker.
$ git clone https://github.com/nfc-tools/miLazyCracker
$ cd miLazyCracker
$ ./miLazyCrackerFreshInstall.sh
In case you don’t know any key to any sector, you can still try the reader attack. For this you will need another piece of hardware, e.g. ChameleonMini RevE Rebooted or Proxmark.
Want to learn more?
Interested in a training regarding security of NFC, Bluetooth Low Energy (Smart), KNX, Linux embedded, and many other topics?
Check out previous and upcoming events or contact us for a private training.
Share this post
Twitter
Google+
Facebook
Reddit
LinkedIn
StumbleUpon
Email