
During upcoming HackInParis 2019 I will present a series of introductory workshops about security of NFC Mifare Classic and Bluetooth Low Energy.
The workshops are short (45min each session), but packed with practical knowledge and hopefully entertaining - performed on a real access control installation, hotel lock and BLE smart locks.
Most hands-on exercises will be possible to complete using just a phone, and easy to follow.
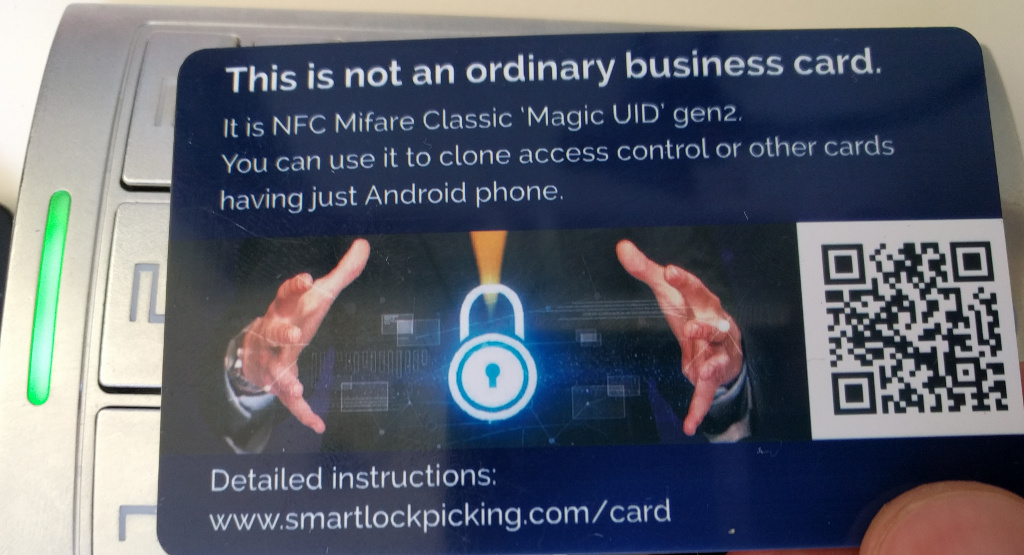
Many access control systems still rely just on the UID of the card. It is a unique number, generated during manufacturing, read-only and impossible to change.
There are however special, unofficial “Magic UID” cards (like my business card) that allow to set any UID - clone it from other cards.
It takes just a few seconds with the new “one click” cloning feature that I have contributed to free Mifare Classic Tool Android application.

During this training we will focus on two technologies implemented very commonly in various IoT devices, including among others smart locks and access control systems : BLE and NFC/RFID.
Bluetooth Low Energy (Smart, 4) is one of the most popular and rapidly growing IoT technologies. Unfortunatelly the prevalence of technology does not come with security, and the knowledge on how to comprehensively assess such devices seems very uncommon. This training aims to address this need.

