Deepsec training
Smart lockpicking - hands-on exploiting contemporary locks and access control systems
There is no doubt electronic locks are among the most profitable smart devices to attack. And yet recent disclosures of multiple vulnerabilities clearly show there are not enough specialists able to help with software-related issues of so-far mostly hardware vendors. This course is intended to fill this skills gap. Based on hands-on exercises with real devices (a dozen various smart locks), attendees will learn how to analyze their security and design them properly. The knowledge will then be applied to many other IoT devices.
During this course students will perform: wireless sniffing, spoofing, cloning, replay, DoS and authentication and command-injection attacks. Practical exercises will include investigating proprietary network protocols, demystifying and breaking “military grade encryption”, abusing excessive services, triggering fallback open, brute-forcing PINs via voice calls and attacking building automation systems.
The software activities will be mixed with short entertaining tricks, including opening a lock by a strong magnet, counterfeiting fingerprints in a biometric sensor or opening a voice-controlled lock by remotely hacking speaker-enabled devices.
Several tasks will evolve around an electromagnetic lock guarding a special vault. Whenever a student will succeed in hacking the lock, the box opens automatically, and one can have a hidden reward.
Technologies covered will include Bluetooth Smart, Linux embedded, KNX, NFC, Wiegand, WiFi, P2P, GSM etc.
Each attendee will receive hardware with a value of about 100 EUR (detailed below).
List of topics
Bluetooth Smart - based on at least 7 various smart locks, and tools developed by the trainer: GATTacker BLE MITM proxy and deliberately vulnerable Hackmelock (consisting of Android mobile application and lock device simulated on Raspberry Pi):
- passive sniffing
- static authentication password
- spoofing
- replay attacks
- command injection
- Denial of Service
- cracking “Latest PKI technology”
- other flaws of custom challenge-response authentication
- abusing excessive services (e.g. module’s default AT-command interface).
- weaknesses of key sharing with guests functionality
- takeaway Hackmelock challenges for practicing later at home using provided hardware
NFC - based on hotel electronic door lock, access control reader, ski lift pass and a bus ticket
- clone UID using “chinese magic” card and provided hardware
- cracking MIFARE Classic keys
- cloning card content
- decoding access control data stored on card by a hotel system
- how to emulate contactless cards and open UID-based lock using just a smartphone
Linux embedded - based on wireless door lock, alarm+home automation system and other devices:
- authentication bypass
- information disclosure
- telnet brute-force
- OS command injection
Proprietary network protocols - based on fingerprint sensor device, wireless door lock, alarm system, HVAC controller
- various approaches to analyzing proprietary protocols
- step-by-step understanding packets and attacking - remote management binary communication of fingerprint sensor
- sniffing and decoding administrative credentials
- abusing improper session management (authentication bypass)
- unlock wireless alarm with a single packet
- P2P communication - how to attack devices hidden behind NAT
KNX home automation - an example installation connected to electromagnetic lock
- theory introduction, typical architecture, group address, device address…
- tools: ETS configuration suite vs open-source - knxd, knxmap, nmap scripts how to locate and connect to KNX-IP gateway in LAN or remotely
- monitor mode - sniffing the bus communication
- write command to group address and open lock
SMS and DTMF remote control over GSM - based on remote control alarm system
- theory introduction to GSM interception
- brute-force alarm administrative PIN via automated remote SMS and voice calls from the cloud API
Wiegand - wired access control transmission standard
- sniff the data transmitted from access control reader using Raspberry Pi GPIO
- decode card UID from sniffed data, clone the card
- replay card data on the wire to open lock
Moreover, each student will also be able try for himself to:
- open a smart lock using special strokes of a strong magnet which turns the motor inside the device
- cheat on a fingerprint biometric sensor - we can make your own fingerprint clone during training
- open a voice-controlled lock by hacking a nearby speaker-enabled device
Pre-requisites
- Contemporary laptop capable of running Kali Linux in virtual machine, and USB port.
- Android > 4.3 smartphone (not crucial, but helpful). If you don’t have one, please inform in advance - a few will be available for students.
- At least basic familiarity with Linux command-line, Kali, Wireshark.
- Scripting/programming skills will be very helpful.
- Mobile application reversing skills will be an advantage.
Target audience
- Pentesters, security professionals
- IoT developers
- Anyone interested
What will be provided?
-
course materials in PDFs (several hundred pages) -
all required additional files: VM images, source code, documentation, installation binaries... -
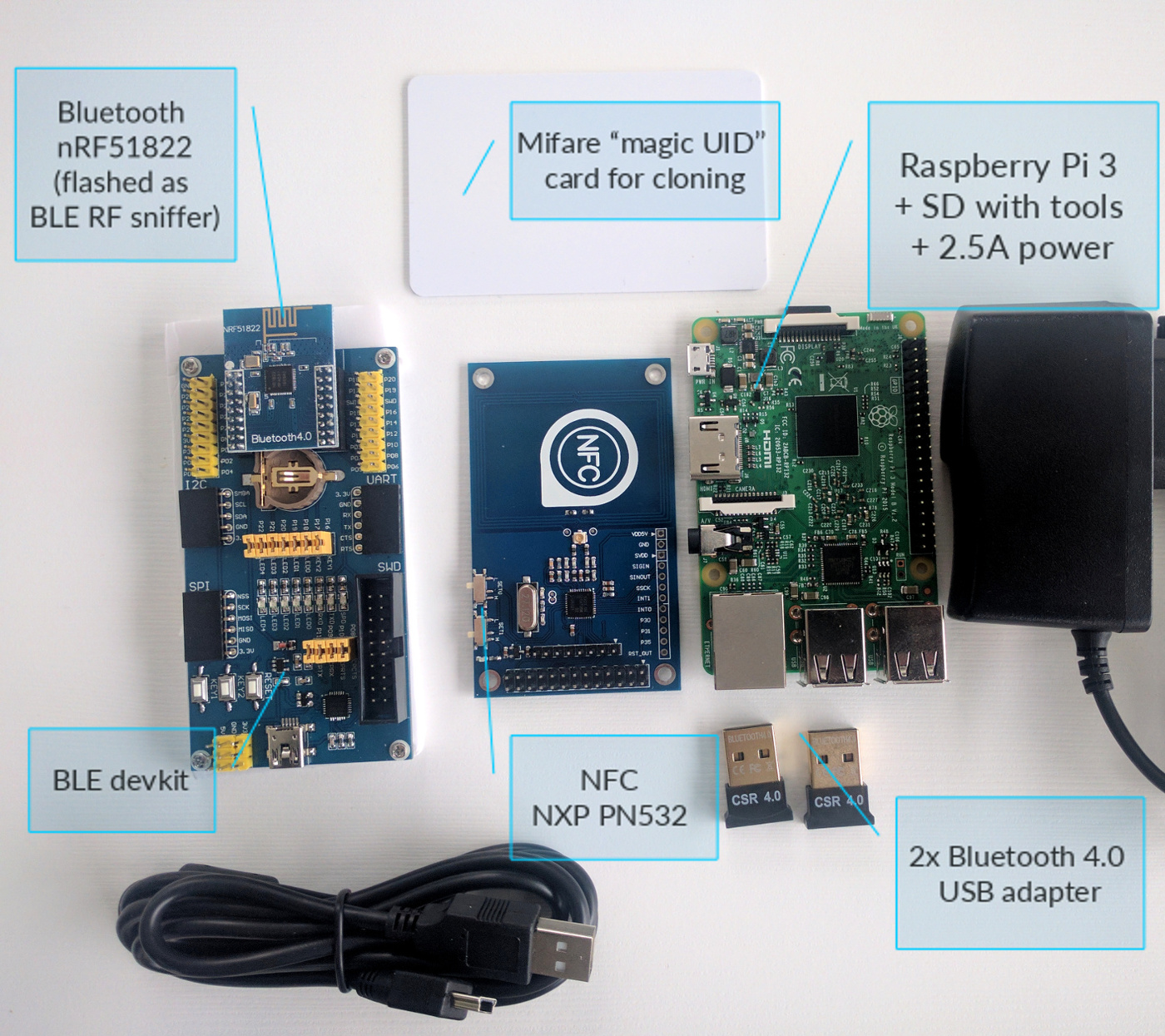
Bluetooth Smart hardware sniffer and development kit based on nrf51822 module -
2 Bluetooth Low Energy USB dongles -
Raspberry Pi 3 with assessment tools and Hackmelock for further hacking at home -
NFC NXP PN532 board + "magic UID" card - which will allow you to clone most common Mifare Classic contactless cards
Register here: https://deepsec.net/register.html
Conference site: https://deepsec.net/speaker.html#WSLOT318
Share this post
Twitter
Google+
Facebook
Reddit
LinkedIn
StumbleUpon
Email